We have three main technologies as follows:
- (1) Asynchronous-Logic
- (2) Side-Channel Attack (SCA) Countermeasures on Dual-Hiding (+Masking)
- (2) Camouflage IC
Asynchronous-Logic
Async2Secure in part employs Asynchronous-Logic as a technology means to enhance the Hardware Security of ASICs/FPGAs. The basic mechanism of asynchronous-logic is to have a data synchronization based on localized handshaking protocols as opposed to that based on global clock infrastructure. Figure below depicts the asynchronous data propagation (D1 to D2 to D3) through the Dual-rail logic circuit and latches (L1 and L2) using the handshake signals (HS) generated by completion detection (CD).
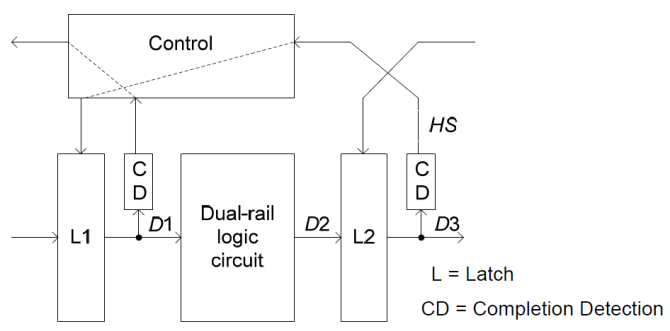
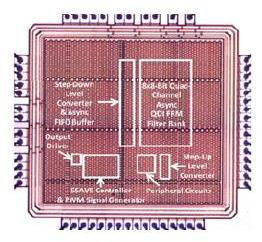
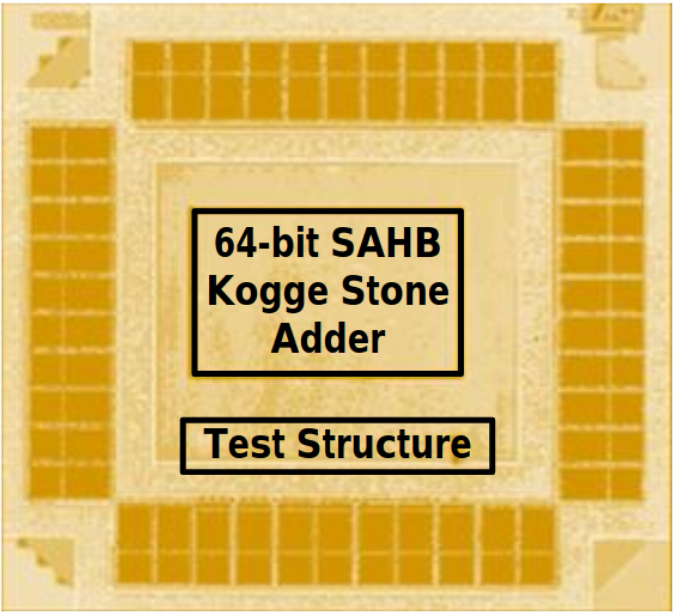
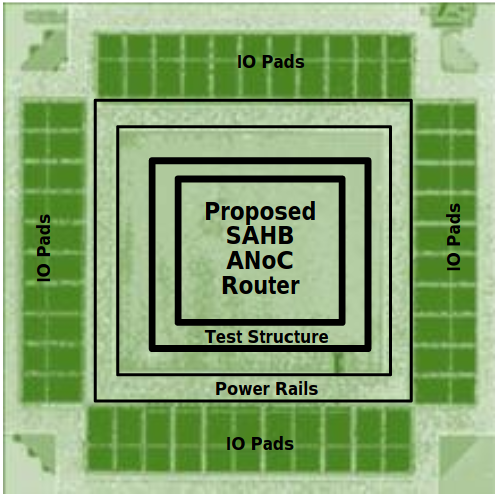
Most of asynchronous-logic research works adopted by Async2Secure were largely conducted in Nanyang Technological University, Singapore. Some microphotographs of the asynchronous-logic prototype microchips are depicted as below. For more information, please click on the links to access the research publications of these works.
Side-Channel Attack (SCA) Countermeasures on Dual-Hiding (+Masking)
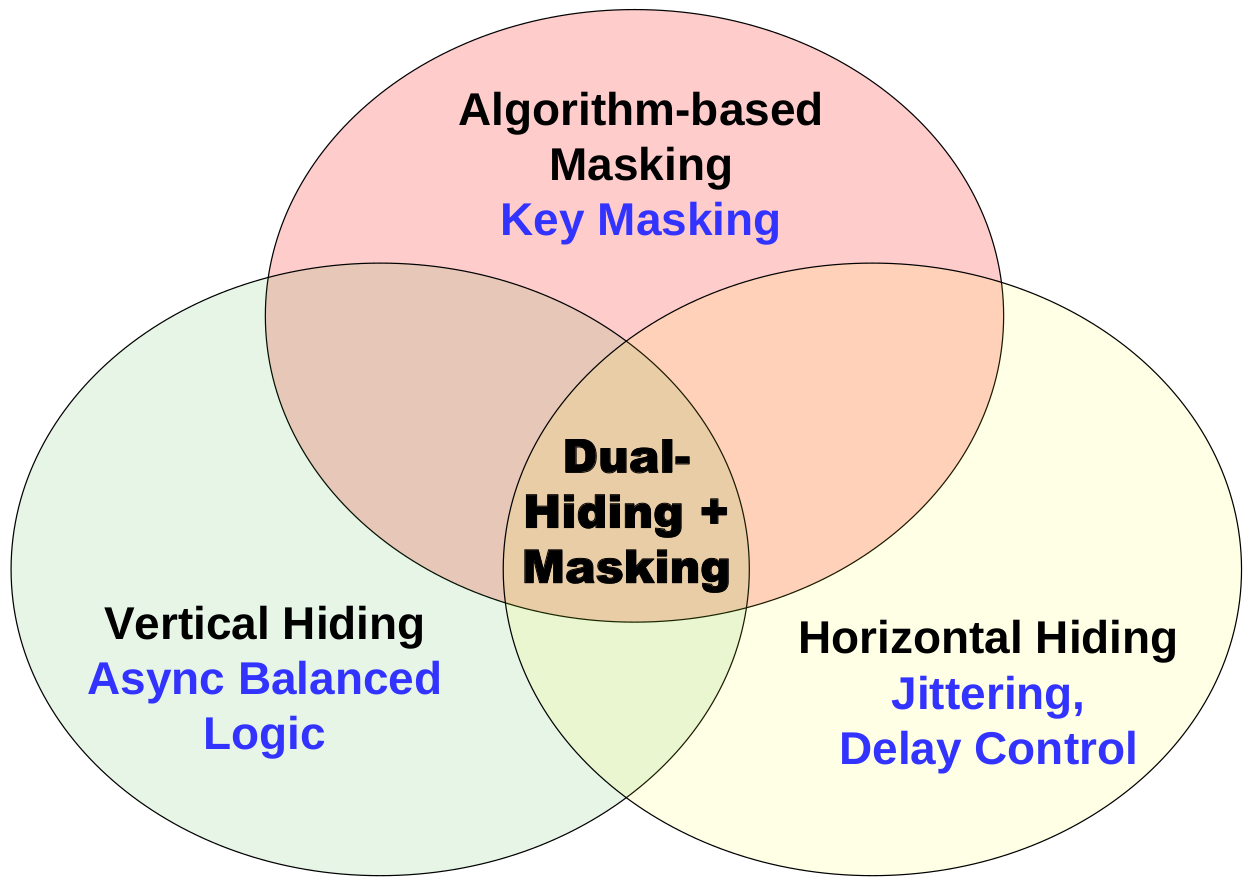
Async2Secure adopts Dual-Hiding + Masking approaches to achieve high SCA-resistance and yet low power/area overheads for cipher designs (including Advanced Encryption Standard (AES)). The primary enabler is in part to use asynchronous-logic to ‘hide’ or moderate the amplitude and timing information on the power or electromagnetic profiles. The conventional Masking approach is also included to add additional protection to counteract SCA. Async2Secure makes the operation of the asynchronous-logic handshaking to achieve the possible ‘best’ dual-hiding optimization.
Camouflage IC
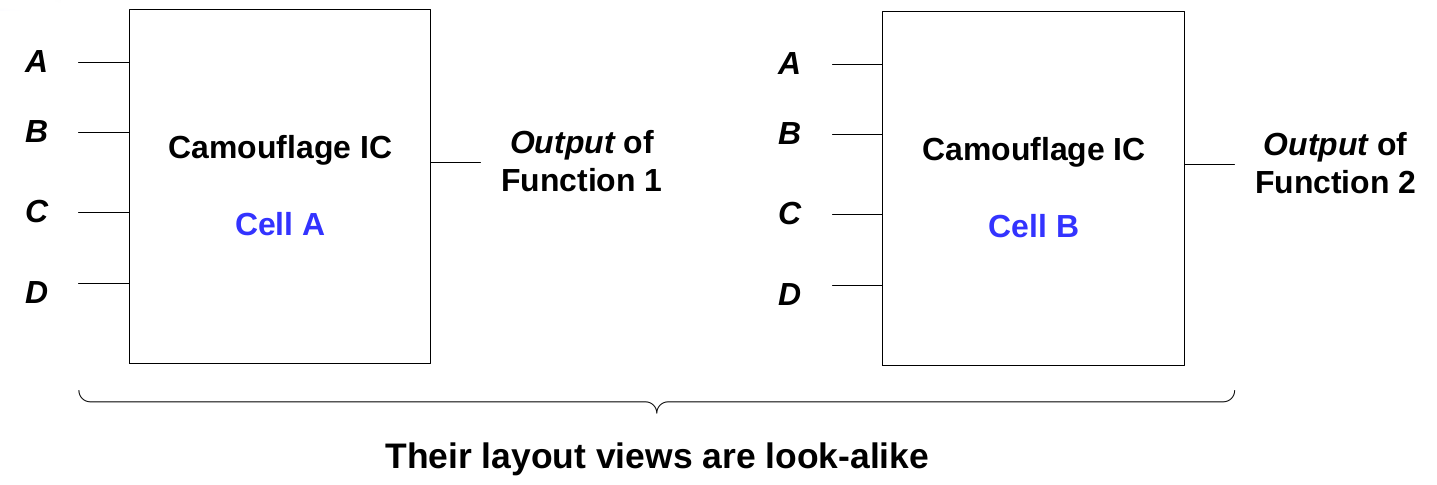
Async2Secure employs patent-pending Camouflage Digital Cells circuit design technique. The basic idea is to make at least two or more digital cells having a look-alike layout view but with different functions. These camouflage digital cells are also intelligently inserted in a netlist in strategic locations where the outputs of these camouflage digital cells have a high output corruptibility rate. Asynchronous-logic implantation can be even used to make the full/partial brute-force netlist analysis impossible. Collectively, the camouflage digital cells with their associated netlist placement and asynchronous-logic implementation provide highly secured protection to the IC design intellectual property to countermeasure against Reverse Engineering.